what is Blu-ray ?
Blu-ray is the successor to DVD. The standard was developed collaboratively by Hitachi, LG, Matsushita (Panasonic), Pioneer, Philips, Samsung, Sharp, Sony, and Thomson. It became the default optical disk standard for HD content and optical data storage after winning a format war with HD-DVD, the format promoted by Toshiba and NEC.
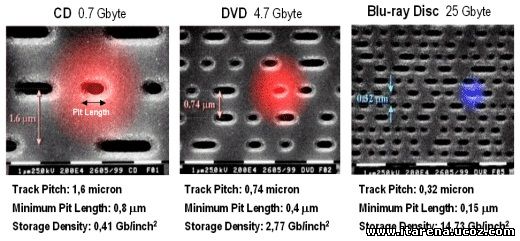
The format's name comes from the fact that a blue laser reads from and writes to the disc rather than the red laser of DVD players. The blue laser has a 405 nanometer (nm) wavelength that can focus more tightly than the red lasers used for writable DVD. As a consequence, a Blu-ray disc can store much more data in the same 12 centimeter space. Like the rewritable DVD formats, Blu-ray uses phase change technology to enable repeated writing to the disc.
Blu-ray's standard storage capacity is enough to store a continuous backup copy of most people's hard drives on a single disc. Initially, the format had a 27 gigabyte (GB) single-sided capacity and 50 GB on dual-layer discs. Single-sided Blu-ray discs can store up to 13 hours of standard video data, compared to single-sided DVD's 133 minutes. In July 2008, Pioneer announced that they had found a way to increase capacity to 500 GB by creating 20-layer discs. These discs are not, however, expected to be commercially available in the near future.
WHAT IS ROLE OF .DLL FILES IN WINDOWS ?
An example would be if the program (exe) needs to get the free space of your hard drive. It can call the DLL file that contains the function with parameters and a call function. The DLL will then tell the executable the free space. This allows the executable to be smaller in size and not have to write the function that has already exists.
This allows any program the information about the free space, without having to write all the source code and it saves space on your hard drive as well. When a DLL is used in this fashion are also known as shared files.
The advantage of DLL files is that, because they do not get loaded into random access memory (RAM) together with the main program, space is saved in RAM. When and if a DLL file is called, then it is loaded. For example, you are editing a Microsoft Word document, the printer DLL file does not need to be loaded into RAM. If you decide to print the document, then the printer DLL file is loaded and a call is made to print.
All in all a DLL is an executable file that cannot run on its own, it can only run from inside an executable file. This would be like having a car without an engine, where as an executable has an engine.
To do load a DLLl file, an executable needs to declare the DLL function. A DLL may have many different functions in it. Then when needed the call is made with the required parameters.
Here is what a Declaration and call might look like in a executable file. This example is simplified so that you might understand it better:
Now lets run a program and make the call.
The DLL is not loaded into RAM until the next line.
* GetFreeSpacex "C",Buffers_If_Any, Drive_Letter
Now let's tell the user how much free space is on drive C
* Use a MessageBox = "The free space on drive C: is ", Value_Returned, "bytes"
& This call required 3 lines of code. Where as if you did not call the DLL file it may have taken you 30 or 40 lines of code.
After knowing about .dll files one more question comes in mind .
Why there are no .dll files in linux ?
hope we will find answer of it and post it soon.
ALL ABOUT REGISTRY
What Is The Registry ?
* In Windows 2000 and Windows XP, the Registry is stored in several Hives, located in the \windows\system32\config and \Documents and Settings\{username} folders.
Structure of the Registry
There are six main branches (five in Windows 2000 and Windows XP), each containing a specific portion of the information stored in the Registry. They are as follows:
* HKEY_CURRENT_USER - this branch points to the part of HKEY_USERS appropriate for the current user.
* HKEY_LOCAL_MACHINE - this branch contains information about all of the hardware and software installed on your computer. Since you can specify multiple hardware configurations, the current hardware configuration is specified in HKEY_CURRENT_CONFIG.
* HKEY_USERS - this branch contains certain preferences (such as colors and control panel settings) for each of the users of the computer. In Windows 95/98/Me, the default branch here contains the currently-logged in user. In Windows 2000/XP, the default branch here contains a template to be used for newly-added users.
* HKEY_CURRENT_CONFIG - this branch points to the part of HKEY_LOCAL_MACHINE appropriate for the current hardware configuration.
* HKEY_DYN_DATA (Windows 95/98/Me only) - this branch points to the part of HKEY_LOCAL_MACHINE, for use with Windows' Plug-&-Play subsystem.
This is all basic information about registry.
the PC means that one person’s machine can be different from another. While games consoles all contain the same hardware, PCs don’t: the massive range of difference can make gaming a headache.
To alleviate as much of the pain as possible, Microsoft needed to introduce a common standard which all games and multimedia applications could follow – a common interface between the OS and whatever hardware is installed in the PC, if you like. This common interface is DirectX, something which can be the source of much confusion.
DirectX is an interface designed to make certain programming tasks much easier, for both the game developer and the rest of us who just want to sit down and play the latest blockbuster
How it works
haven’t had to make any complex configuration changes.
How antivirus software works?
Each of these modules are quite complex in functionality and integrates with the respective part of the operating system to provide protection. Like Real Time Protection is based on file system driver at its core. It intercepts all the file activities happening in the system
and makes sure that the file that is being accessed is clean. Email protection is based on network and communication driver at its base which intercepts the email communication to scan all the emails that are being sent or received.
Most important component the Anti-Virus Engine consists of lots of modules like file format identification and parsing, un-archivers and un-packers, signature scanners, emulators etc. In simple words AV Engine’s primary task is to scan a file for virus and presence of other malwares by, first scanning it for presence of virus definitions (signatures). After that engine also applies various scanners on the file based on the type of the file and the contents of the file. Like polymorphic virus detection engine, generic malware symptoms detection etc. Also there is a component in most of the AV engines called as heuristic scanner which is also applied on the file for detection of new unknown malwares.
Google Search Technology
PageRank Technology
Hypertext-Matching Analysis
Why We Require Device Driver's ?
In Windows operating systems, a device driver file usually has a file name suffix of DLL or EXE. A virtual device driver usually has the suffix of VXD.
A device driver simplifies programming by acting as an abstraction layer between a hardware device and the applications or operating systems that use it. The higher-level application code can be written independently of whatever specific hardware device it will ultimately control, as it can interface with it in a standard way, regardless of the underlying hardware. Every version of a device, such as a printer, requires its own hardware-specific specialized commands. In contrast, most applications utilize devices (such as a file to a printer) by means of high-level device-generic commands such as PRINTLN (print a line). The device-driver accepts these generic high-level commands and breaks them into a series of low-level device-specific commands as required by the device being driven. Furthermore, drivers can provide a level of security as they can run in kernel-mode, thereby protecting the operating system from applications running in user-mode.
Brief History Of Google
Hi Friends,
"...Google began as a research project in January 1996 by Larry Page, a Ph.D. student at Stanford. Larry was soon joined in his research project by Sergey Brin a fellow Stanford Ph.D. student and close friend. Larry Page hypothesized that a search engine that analyzed the relationships between websites would produce better results than existing techniques (existing search engines at the time essentially ranked results according to how many times the search term appeared on a page). It was originally nicknamed, "BackRub", because the system checked backlinks to estimate a site's importance. A small search engine called RankDex was already exploring a similar strategy.
Convinced that the pages with the most links to them from other highly relevant Web pages must be the most relevant pages associated with the search, Page and Brin tested their thesis as part of their studies, and laid the foundation for their search engine. Originally the search engine used the Stanford website with the domain googol.stanford.edu. However when they got their first pay cheque soon after commercialising the idea, the banker made a cheque in the name of Google instead of Googol. Hence the name "google" originated. The domain google.com was registered on September 15, 1997. They formally incorporated their company, Google Inc., on September 7, 1998 at a friend's garage in Menlo Park, California..."
Did U Know....?
We all have our E-mail ids...while creating them i.e while filling out the registration form we need to fill a box with exactly the same words and numbers mentioned nearby..as an example "C9DeY"....but why do we need it??
And answer to this is......
How would you differentiate a human & a computer on the internet?
How would you differentiate a 'bot' (internet robots) from a real person?
How would you prevent someone from running automated scripts which would create fake ids on email servers?
The answer comes from CAPTCHA - Completely Automated Public Turing test to tell Computers and Humans Apart.
The technique implements a distorted image consisting of digits & letters which can be understood only by a human eye. The person filling out the registration form is asked to enter the alpha-numeric combination which appears in the image. Therefore, even if a script is run to fill the registration form; it will fail because the image verification will fail.
Of course, a new set of letters & numbers is selected every time. The reason is obvious, isn't it? We do have the same technique to prevent fake registrations.
The images are a random combination of font, size, orientation, colour and location of each indvidual character. Once this combination is generated, the data pertaining to the image is saved from display memory i.e. what we see on screen and not from data memory, which is set of characters with attributes mentioned.
Why different fonts, colour.....? There are image recognition softwares which can identify text. We simply need to generate a very complex pattern which a human can understand but a software might not.
Does this mean that the techinique is fool proof??? Most of these images have different characters in different colours. A cue to isolate and identify each character. Then we can always know which character follows what.
To verify this, I used an image2text software and found that more than 70% of times the software actually manages to identify text properly but its the inbuilt dictionary which generally spoils the show by trying to make some sense of things it has read.
So, are you fully protected from automated scripts filling your forms??? For now, almost yes but beware...software grows real fast and people will come out with some newer techiniques.
How To Tackle Viruse's When Your Antivirus Fail's
One of the best ways to protect yourself from viruses is from proactive defense. Among college students, virus propagation is greatest through USB flash drives. When they plug them back into their own computer or laptop, the virus goes straight into action.
To stop that, use programs such as TweakUI to disable the autorun function. Next, always scan the drive before opening it. However, sometimes scanning isn't always practical because your USB may contain a gigabyte or more of data. What you can do is right-click and click on "Explore" instead of "Open". Then, make sure "Show Hidden Files" option is selected. Viri and their autorun files usually reside at the "root" of the USB, so you can immediately spot them and delete them.
There are some instances that the "Explore" function is hijacked by the autorun file as well as the "Open" function. You'll know this if it is bold in text. In that case, access the drive through a file exploring program.
What we can suggest is that you put all your files in a folder (or a few folders) in the USB. That way, you can easily see any program that installs itself on the root of the USB drive. Also, even if you cannot stop virus files installing themselves on the USB, you can stop their "autorun" files being placed as well. You can create "fake" autorun files that cannot be over written by virus ones . A program that can do that is this (Flash Disinfector « eXPeri3nc3’s Corner). That program can also fix some errors caused by virus.Its good to start with USBs as they are the common but risky mode of transferring data these days.
First of all, cancel the autoplay option(appears when you plug in your USB) asking you to "open folders to view files", "take no action" etc.
This decreases the chances of virus spreading.
Now, some of the common viruses that are spreading through USBs:
- Ravmon.exe
- New Folder.exe
- Orkut is banned
The following steps may help you remove some of common viruses:
1. Open the command prompt.
Start>Run>cmd
2. In the command prompt, type the drive letter(eg. G: ) and press
enter. This will display a list of the files in the pen drive. Check
whether the following files are there or not
- Autorun.inf
- Ravmon.exe
- New Folder.exe
- svchost.exe
- Heap41a
- or any other exe file which may be suspicious.
3. In command prompt type attrib -r -a -s -h *.*
and press enter. This will remove the Read Only, Archive, System and
hidden file attribute from all the files. Now just delete the files